
Exploring the Benefits and Challenges of Asymmetric Key Cryptography
Asymmetric key cryptography, also known as public-key cryptography, is a cryptographic system that uses two keys, a public, and a private key, to secure communication and data transmission. In this system, the public key is widely distributed and used to encrypt data, while the private key is kept secret and used to decrypt the data.
A brief review of Asymmetric Key Cryptography’s History
Asymmetric key cryptography can be traced back to the early 1970s when Whitfield Diffie and Martin Hellman published their seminal article “New Techniques in Cryptography.” This event is considered to be the catalyst for developing asymmetric key cryptography. This type of cryptography allows an author to encrypt a message by employing the recipient’s public key, while the recipient can decrypt the message using their private key.
Clifford Cocks and Malcolm Williamson, both working as researchers at the Government Communications Headquarters (GCHQ) in the United Kingdom in 1976, independently came up with the same idea of public key cryptography not long afterward. Despite this, their attempts were kept secret for many years.
The RSA algorithm was developed in 1977 at the Massachusetts Institute of Technology (MIT) by Ron Rivest, Adi Shamir, and Leonard Adleman. It is still widely utilized in asymmetric key cryptography today. To ensure the confidentiality of the safeguarded communications, the RSA method uses the challenging task of performing multiplications on very large integers.
Since its discovery, asymmetric key cryptography has developed into an essential part of the modern communication and e-commerce networks used today. It is used to protect confidential information such as credit card details and personal identification numbers (PINs), as well as to safeguard communication channels.
Asymmetric Key Cryptography: How does it work?
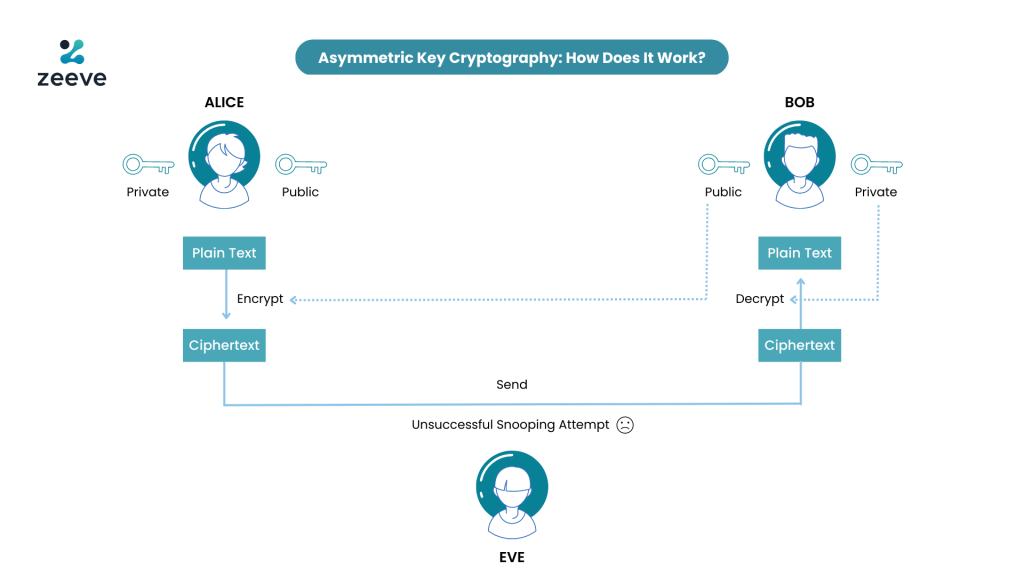
The procedure is as described below:
Generation Of Key Combination
The generation of the key combination is the first stage in asymmetric key cryptography. While it is the recipient’s responsibility to keep the private key hidden from anyone who might want to send an encrypted communication to the recipient, the public key is typically made accessible to anyone who might like to send such a communication.
Encryption of Message
When encrypting a message with asymmetric key cryptography, the news creator must use the recipient’s public key for the encryption process to be successful. This ensures that the communication can only be deciphered by the recipient, as they are the only ones with access to the corresponding private key.
Decryption
When the recipient receives the message that has been encrypted, they will use their private key to retrieve the message once it has been delivered to them. Only the person who was supposed to receive the encrypted communication can decipher it because the private key is kept secret and is never shared with any other person.
Digital Signature
Asymmetric key cryptography can be utilized to generate digital signatures, which are then put to use in the process of determining whether or not a communication is genuine. Asymmetric key cryptography is capable of supplying digital identities when needed, and to generate a digital signature, the sender encrypts a message with their private key, and the recipient decrypts it with the sender’s public key to read the message. If the encrypted message and the original message are the same, this demonstrates that the originator was the message’s author and that it has not been changed in any way.
Asymmetric Encryption Algorithms
The following are asymmetric encryption methods that are used frequently:
RSA Algorithms
Rivest-Shamir-Adleman, abbreviated as RSA, is a method for public-key cryptography that was presented for the first time in 1977 and has since gained widespread adoption. It is very difficult to break cryptography. After all, it is so secure because it is based on the difficulty of calculating large prime numbers.
Diffie-Hellman Algorithms
Diffie-Hellman (DH) is an algorithm for the exchange of keys that allows two parties to agree on a shared secret key without ever actually transmitting the key itself. This is made possible by DH’s ability to prevent the transmission of the key itself. As a precautionary measure, asymmetric encryption is frequently utilized in conjunction with creating confidential communication channels.
ECC algorithms
Elliptic Curve Cryptography, abbreviated as ECC, is a public-key cryptography method mathematically derived from the idea of elliptic curves. Its ubiquitous implementation in mobile and Internet of Things devices can be attributed to the fact that it can offer a high level of security despite having relatively diminutive key sizes.
Digital Signature Algorithm (DSA)
The Digital Signature Algorithm, also referred to as DSA, is an example of a digital signature technique that can be applied to validate the genuineness of a communication or document. It is predicated on how difficult it is to compute discrete logarithms in a field containing only a finite number of elements. Specifically, it is predicated on how difficult it is.
ElGamal Algorithms
The Diffie-Hellman key exchange is the basis for ElGamal, a public-key cryptography technique based on that exchange. Applications that require cryptography and digital identities typically use it as a necessary component because those applications require it.
Benefits and Disadvantages of Asymmetric Key Cryptography
Asymmetric key cryptography has several benefits, some of which are as follows:
- The ability of asymmetric key cryptography, which can encrypt data using two different keys, provides a foolproof method for sending sensitive data over untrusted networks, such as the internet. This is because the process encrypts the data using both keys simultaneously.
- Asymmetric key cryptography is also used to provide digital signatures, which are useful for authenticating the sender’s identity and ensuring that the message has not been altered. Digital signatures are provided by asymmetric key cryptography. Asymmetric key cryptography is what enables digital identities to be generated.
- By utilizing asymmetric key cryptography, one can acquire a method of key dissemination that is both secure and private. A randomization is an option for producing keys. Given that the public key can be widely distributed, it is possible to encrypt a private key and then send it on to the person to whom it is addressed. This is made possible because the public key can be widely shared.
The following is a list of disadvantages associated with asymmetric key cryptography:
- When compared to symmetric key cryptography’s procedure, asymmetric key cryptography’s intrinsic delay can be attributed to the complexity of the techniques that are employed within it.
- Asymmetric key cryptography is more sophisticated than symmetric key cryptography, which can be more difficult to implement and manage than symmetric cryptography.
- Properly operating asymmetric key cryptography depends on carefully managing public and private keys. The entire system’s security can be undermined if a private key is lost, stolen, or otherwise infiltrated in any way.
- Asymmetric key cryptography is vulnerable to attacks such as man-in-the-middle attacks, in which an adversary intercepts and modifies messages that are being exchanged between two parties. Nevertheless, by utilizing digital identities in combination with other forms of protection, this danger can be minimized.
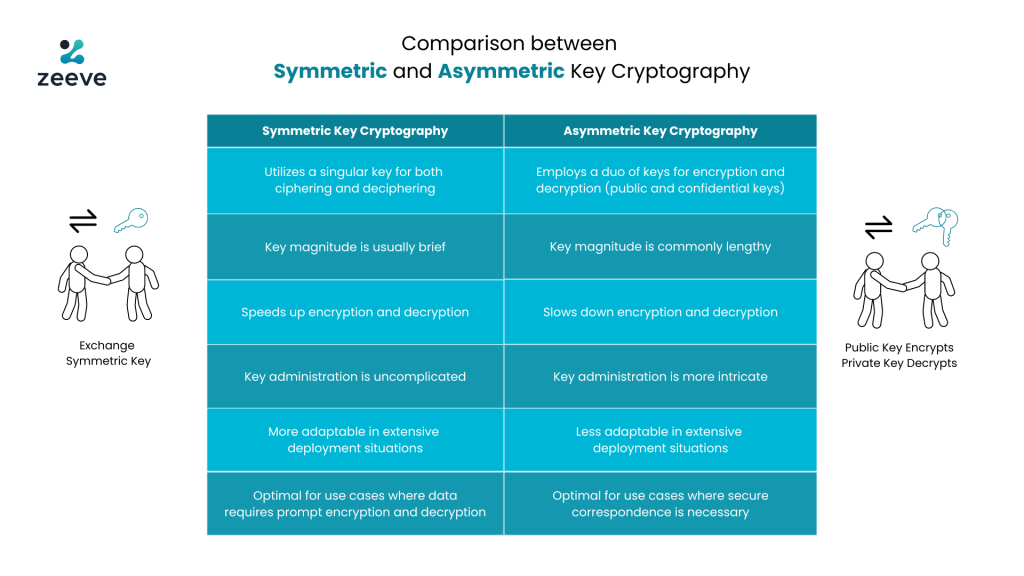
Comparison of Symmetric and Asymmetric Key Cryptography
Application of Asymmetric Key Cryptography in Real Life
Asymmetric Key Cryptography has various practical uses, such as:
- Safe Online Transactions: One of the primary uses of Asymmetric Key Cryptography is to secure online purchases. The SSL/TLS protocol, which protects online transactions, uses Asymmetric Key Cryptography to encrypt the information passed between a website’s server and a user’s browser. This helps prevent the theft of important information, such as credit card numbers, by intercepting it.
- Asymmetric Key Cryptography is also employed to protect email communications. This ensures that only the intended recipient can view the contents of the email. The email is encrypted using the public key of the recipient and is decrypted using the recipient’s private key.
- Digital Signatures: Asymmetric Key Cryptography is used to produce digital signatures. A digital signature validates that a document was created by a specific individual and was not altered. The sender’s private key generates the signature, which can be validated using the sender’s public key.
- Secure Document Distribution: The use of advanced cryptographic techniques, specifically Asymmetric Key Cryptography, allows for the safe distribution of documents between parties. The sender can encrypt the document using the recipient’s public key, and the recipient can then decrypt it using their private key. Only the intended recipient can access and view the document’s contents.
- Private Virtual Networks (PVNs): PVNs utilize advanced cryptographic techniques, specifically Asymmetric Key Cryptography, to encrypt data transmitted between a PVN server and a user’s device. This encryption helps protect the sent data from interception and prevents unauthorized entities from reading it, thus enhancing the privacy and security of the transmitted data.
Final Review
Asymmetric key cryptography is an efficient method that has had a significant influence not only on how we communicate with one another but also on how we safeguard confidential information.
As opposed to symmetric cryptography, it possesses several advantages, but on the other hand, it is also plagued by a certain amount of disadvantages. To put it another way, it is not perfect in any way.
Despite this, it offers a high level of security and confidentiality, which, when it is correctly implemented and maintained as a key pair, makes it an important instrument for modern cryptography. Despite this, it offers a high level of security and confidentiality. To read more about cryptography, or anything blockchain, its infrastructure, and automation keep following Zeeve.





Responses